Frameworks
ISO 27001
Advanced CISO Guide to ISO 27001 in Middle East FinTech: Beyond the Audit
Jan 26, 2026
FinTech | Trust | Middle East
Trust is everything in FinTech. One breach, one compliance failure, and it’s gone. With security under constant scrutiny, CISOs and CTOs turn to ISO 27001 to protect their credibility. It’s how you stay ahead of regulators, earn the board’s trust, and keep the business secure.
This guide skips the basics. It’s for CISOs ready to use ISO 27001 as a lever for strategic influence - quantifying risk in business terms, aligning security with board KPIs, and embedding your ISMS into the tech shaping tomorrow’s finance.
Translating Risk into Revenue: The CISO's Business Case
Your job isn’t just security - it’s making its value clear in business terms. Move from abstract threats to quantifiable financial impacts. Advanced risk assessments enable that shift.
FAIR (Factor Analysis of Information Risk) enables you to model cyber risk in financial terms. Rather than vague warnings, you can quantify potential losses - such as stating a breach could cost USD 5 million over 12 months based on incident response, fines, and churn under PDPL - helping translate technical threats into business impacts.
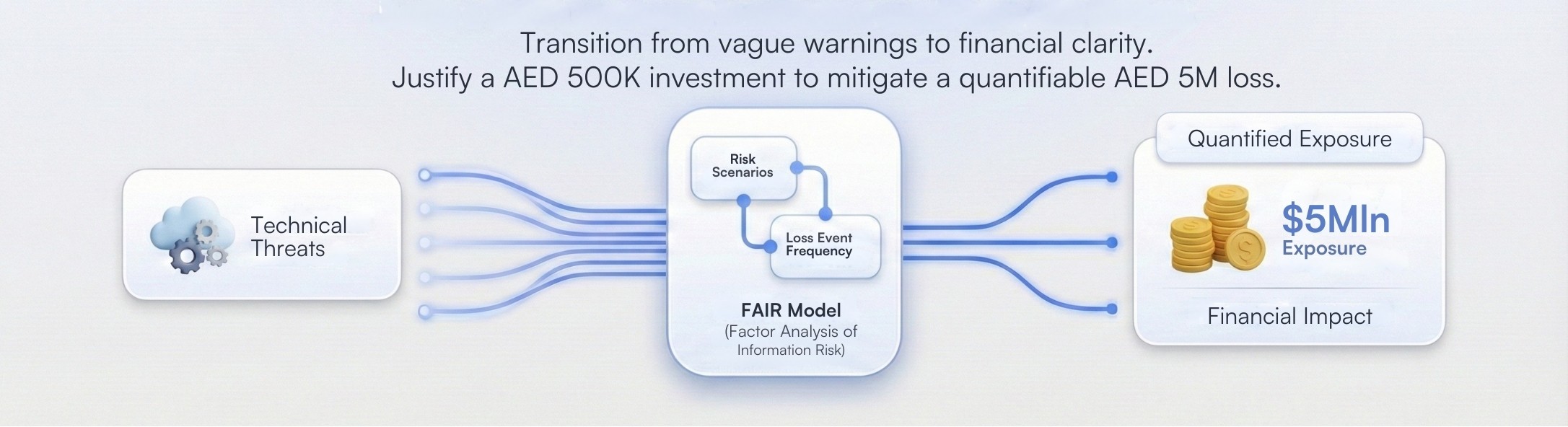
Quantitative risk assessment lets you justify security investments, secure executive support with clear financial data, and prioritize controls that actually reduce business risk.
Quantified Risks help:
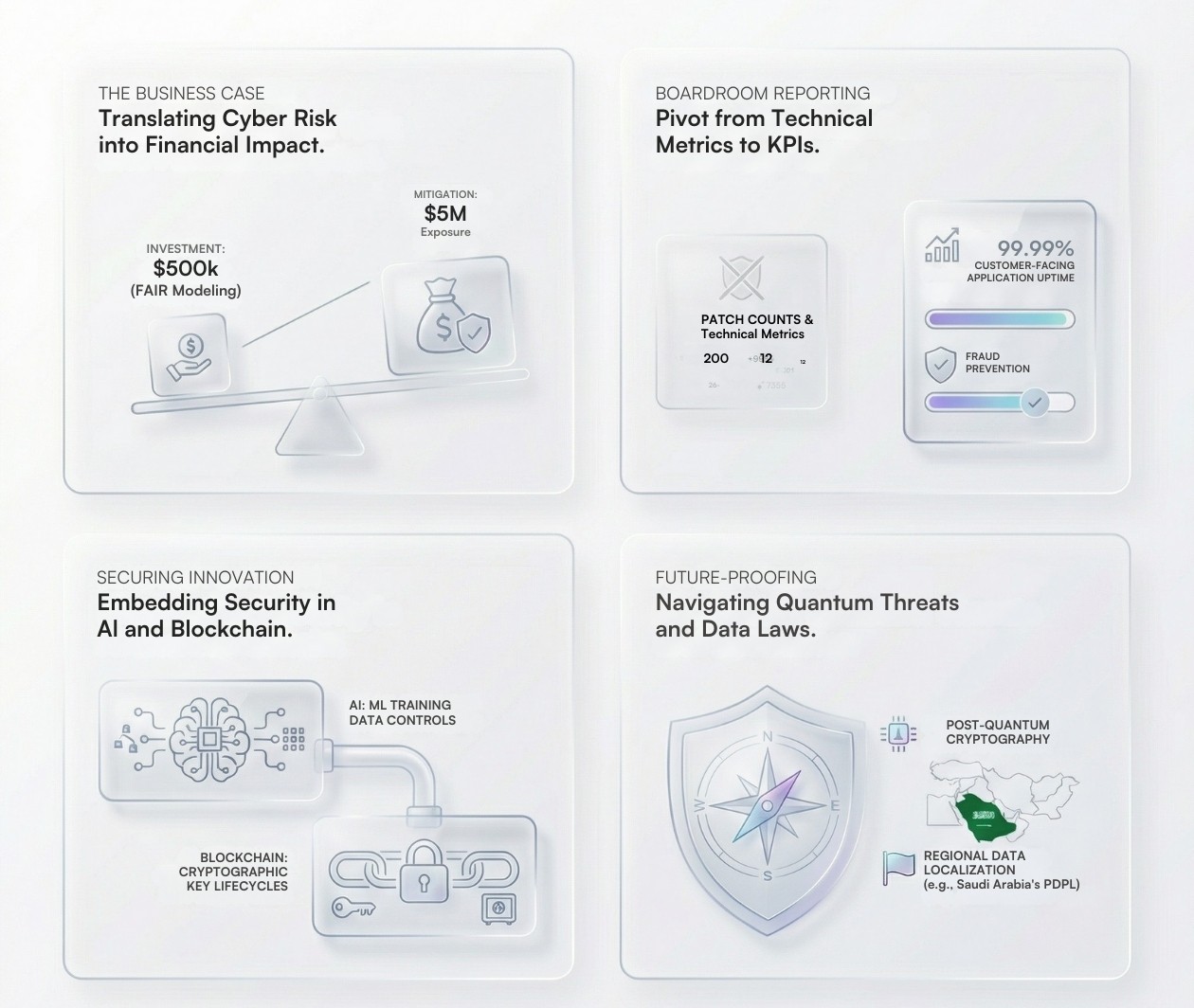
Justify Security Investment: When you present a risk treatment plan that reduces a USD 5 million exposure to an acceptable level for a USD 500,000 investment in advanced encryption and zero-trust architecture, you are making a clear business case, not a technical plea.
Secure Leadership Buy-in: Boards and executive teams respond to data. Financial modeling gives them the information they need to make informed decisions and allocate resources appropriately. It transforms security from a cost center into a function that directly protects revenue and brand equity.
Prioritize Controls: It enables you to prioritize security controls based on their potential to reduce financial loss, ensuring resources are allocated to the most critical risks.
For top players in Saudi Arabia, risk maturity isn’t optional - it’s fundamental for proving to investors and partners the business is secure and built for longevity.
From Security Metrics to Business KPIs: Reporting to the Board
Standard security metrics, like the number of patches or alerts, don’t resonate with the board. Instead, frame your ISMS performance around what matters: growth, efficiency, and uptime. Show how security directly enables revenue, market expansion, and operational reliability.
Align your ISO 27001 program with business KPIs.
Instead of: Number of phishing simulations completed.
Report on: Reduction in business email compromise attempts that lead to financial loss, directly impacting the bottom line.
Instead of: Time to patch critical vulnerabilities.
Report on: Percentage of customer-facing applications free of critical vulnerabilities, linking security directly to customer trust and service availability.
This reframing shows security as a business driver. Reporting on uptime and fraud prevention - outcomes the board values - demonstrates how an effective ISMS supports revenue and reliability, not just technical compliance.
Integrating ISO 27001 with Emerging Technologies
A static ISMS won’t withstand a landscape shaped by AI and blockchain. As these technologies redefine risk, your ISO 27001 framework must adapt - addressing new attack surfaces, evolving data governance, and ensuring controls keep pace with rapid innovation.
AI and Machine Learning
As firms use AI for fraud detection and credit scoring, the integrity and confidentiality of the models and their training data become critical information assets. Your ISMS scope must expand to include:
A.5.10 (Acceptable use of information and other associated assets): Establish clear policies for handling sensitive data used to train AI models, ensuring it is anonymized and protected throughout its lifecycle.
A.8.25 (Secure development lifecycle): Integrate security controls into the MLOps lifecycle to protect against model poisoning, data drift, and adversarial attacks during the build and deployment phases.
Blockchain and Distributed Ledger Technology (DLT)
For FinTechs like UAE-based Ziina tackling digital assets and smart contracts, the security focus shifts from traditional databases to robust cryptographic key management and securing consensus mechanisms.
A.8.24 (Use of cryptography): Your policies must address the entire lifecycle of cryptographic keys, including secure generation, storage in hardware security modules (HSMs), rotation, and revocation. Compromised private keys can lead to catastrophic and irreversible losses.
A.8.28 (Secure coding): Controls must be applied strictly to smart contract development. This includes mandatory code reviews and static analysis to prevent logic vulnerabilities that could be exploited to drain funds.
Future-Proofing Your ISMS: Quantum Computing and Cross-Border Data Flows
A forward-looking ISO 27001 program does more than address today’s risks - it anticipates what’s next and ensures your organization is ready to act.
The Quantum Threat
Quantum computing will soon break current asymmetric encryption. Even before large-scale quantum machines arrive, attackers are already storing encrypted data—planning to decrypt it as soon as new technology makes it possible.
As a CISO, your role is to:
Educate the Board: Start raising awareness about the quantum threat and the need for a transition to post-quantum cryptography (PQC).
Inventory Cryptographic Assets: Begin identifying all systems and applications that rely on public-key cryptography.
Plan for Transition: Align your technology roadmap with the standardization efforts of bodies like NIST. The transition to PQC will be a complex, multi-year effort, and planning must start now. Your ISMS will be the governing framework for this transition.
Data Sovereignty and Cross-Border Collaboration
Stricter data localization laws like Saudi Arabia’s PDPL complicate the use of global cloud platforms and international growth. ISO 27001 offers a practical framework for tackling these challenges, helping CISOs set clear cross-border data policies and ensure ongoing compliance.
A.5.14 (Information transfer): This control becomes central. Your policies must define the legal and security requirements for transferring data across borders, specifying approved jurisdictions and technical controls like encryption and tokenization.
A.5.19 (Information security in supplier relationships): Your third-party risk management program must rigorously assess the data handling practices of cloud providers and other vendors, ensuring they can comply with regional data residency requirements.
For firms eyeing international growth, ISO 27001 certification signals to regulators and partners that you can securely manage data across complex, multi-jurisdictional environments.
ISO 27001 as Your Strategic Enabler
For the advanced CISO, ISO 27001 is a strategic leadership tool. It enables you to build resilience, translate risk into business impact, and justify resource needs. By tying it to financial modeling, business KPIs, and emerging tech, you move from technical executor to core business partner.
Reaching this level means shifting from treating compliance as a one-time goal to embracing it as ongoing, strategic risk management. This mindset ensures your organization isn’t just compliant—it’s ready to thrive in a fast-moving market.